What is Machine Learning with Cryptography?
Machine learning is a fast-expanding area with significant applications in a wide range of sectors, particularly cryptography. Cryptography is the art of safeguarding information by transforming it into a code or cipher that is hard to access or read by unauthorized users. In this post, we’ll look at how machine learning may be utilized in cryptography, as well as its advantages and disadvantages.
Machine learning may be used to improve cryptography approaches in a variety of ways. Some examples are:
- Creating Cryptographic Keys
The procedure of creating a secret key that is used to encrypt and decode data is known as cryptographic key creation. To generate more secure and unexpected keys, machine learning techniques may be taught on vast datasets of random number generators. These keys can then be utilized in a variety of cryptographic approaches, such as symmetric and asymmetric key encryption.
- Encryption and Decryption
By studying patterns in data plus detecting possible flaws or problems, machine learning may be used to enhance encryption and decryption algorithms. Machine learning models may also be utilized to create safer and more effective encryption and decryption techniques.
- Anomalies Recognition
The technique of detecting aberrant or unexpected behavior in data is known as anomaly detection. By monitoring network data and recognizing patterns that signal a possible assault, techniques based on machine learning may be used to detect possible security breaches or attacks. This can assist to protect encrypted data from unauthorized access.
How to train ML models on encrypted data?
Developing a machine learning model with encrypted data is a challenging yet essential task to uphold confidentiality of data while leveraging the power of machine learning. One approach to enhance privacy is by leveraging technologies like homomorphic encryption or secure multi-party computing (MPC). Below are the steps for training a machine learning model using encrypted data:
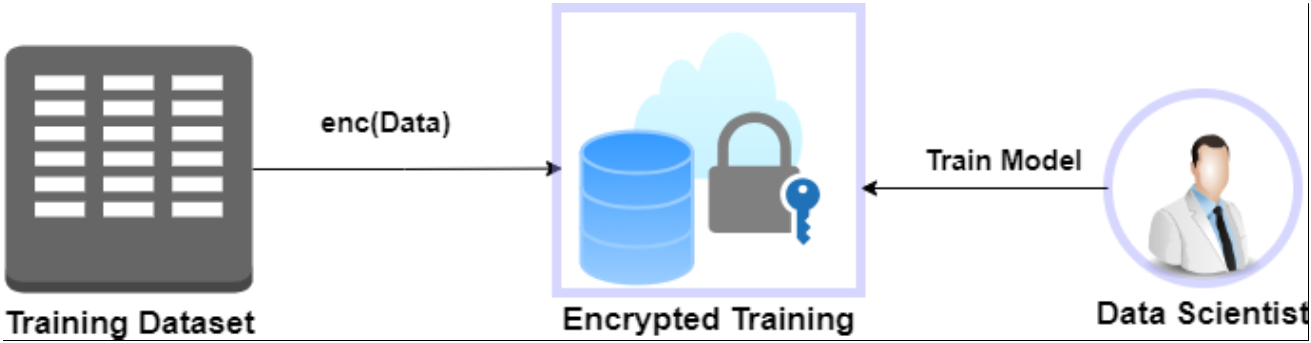
- Data Encryption
Using privacy-preserving encryption technologies, encrypt the private training data. Homomorphic encryption, also known as MPC, allows data to stay secured while allowing calculations to be done on it.
- Selecting Model for Privacy Preservation
Select machine learning methods and techniques that are consistent with the encryption technology being employed. Algorithms with privacy-preserving features may be offered.
- Preprocessing and Feature Technology
On the encrypted data, perform feature design and data preparation operations such as data normalization, reduction of dimensions, and choosing features. These actions are carried out while the data is still encrypted.
- Training
Using encrypted data, train the privacy-preserving machine learning system. Make sure that the algorithm’s variables and any intermediate outcomes are encrypted as well. Iterative procedures to fine-tune the model may be used at this stage.
- Verification and assessment
Using verified datasets, evaluate the model’s effectiveness without disclosing private data. Measure the model’s precision, accuracy, recall, or additional pertinent criteria using suitable assessment measures.
- Optimization
Based on the assessment’s findings, optimize the framework. Modifying hyperparameters, improving the model construction, or fine-tuning other components of the system may be included.
- Installation
Place the learned privacy-preserving machine learning algorithm in an appropriate setting that can handle encrypted data. Depending on the application, this deployment might take place in the cloud or on edge machines.
- Encrypted Data Inferring
Employ the deployed model on encrypted data to make predictions, classifications, or other machine learning-related activities. The model performs operations on encrypted data without actually decrypting it.
- Result Decryption
Decrypt the findings when the model has completed its evaluation using the necessary encryption keys. This stage gives useful insights while concealing the raw data.
- Security Procedures
Provide strict safety protocols to safeguard encryption keys, parameter values, and overall data and model confidentiality. To reduce possible risks, keep encryption methods and security measures up to date.
When interacting with encrypted data, it is critical to have knowledge of both machine learning and encryption. Furthermore, because this technique is computationally expensive, efficient equipment and powerful computing environments may be required. The machine learning techniques utilized should be well-aligned with the unique requirements and limits of the privacy-preserving strategy.
Pros and Cons
Machine learning in cryptography has several benefits, including enhanced security, faster processing, and less human error. The system can analyze large datasets, identify weaknesses, and efficiently process vast amounts of data, enabling real-time applications. Moreover, machine learning can reduce the probability of safety breaches or imperfections.
The application of machine learning in cryptography introduces dangers such as algorithm excessive reliance, possible cyberattacks, and ethical considerations. Overconfidence can lead to an incorrect perception of security, because algorithms are only as good as the data on which they are trained. Cyberattacks can taint outcomes, presenting ethical problems.