Understanding Hashing in Blockchain :

Hashing is similar to putting your data through a magical machine that generates a special fingerprint for each piece of data. No matter how large your data is, this fingerprint, also known as a hash value. It’s a shortened version of it that is always the same length. It’s similar to assigning a unique code to every item of data.
Hashing is an excellent method for determining whether your data has been tempered, safely storing passwords, and maintaining privacy in cryptography. What’s the best thing, then? It is very reliable as well as fast.
HASHING IN BLOCKCHAIN
Hashing is like a secret recipe that turns any type of data into a unique code of fixed length. Once data is hashed, it’s impossible to turn it back into its original form. Also, it’s extremely unlikely for two different pieces of data to produce the same hash code. This makes hashing super useful for things like keeping passwords secure, checking if data has been changed, and organising data in a way that’s quick to find and use. In blockchains, hashing helps ensure that each block in the chain is linked securely to the previous one, maintaining the integrity of the whole system.
A blockchain hash is produced by comparing a block of input data with a previously generated hash value using a cryptographic algorithm. Information is considered unaltered if the hash that was recently computed still matches the data that was supplied.
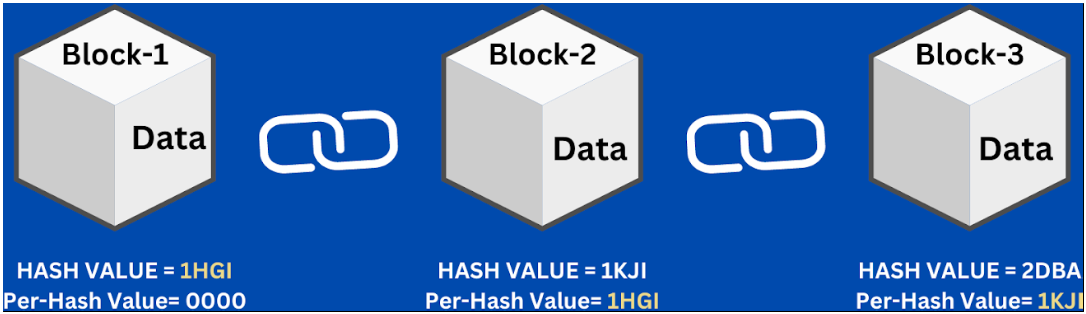
It is not wrong to say that hashing plays a fundamental role in the security of blockchain systems.
Because blockchains depend on the integrity of data. Every block has a hash from the one before it, so each block forms a chain. If you tampered with any of the blocks, it would be like crumpling two separate documents into one ball; it wouldn’t match the chain. Because of this, hashing is essential for protecting and confirming data on the blockchain.
TYPES OF HASHING
Hashing algorithms have a number of types, each with unique properties and applications. The following are a few typical hashing types:
- CRYPTOGRAPHIC HASH FUNCTIONS
These have characteristics like collision resistance and pre-image resistance and are made for use in cryptography. Examples are SHA-3, MD5, and SHA-256 (Secure Hash Algorithm 256-bit), while MD5 is currently regarded as insecure for cryptographic purposes.
- NON-CRYPTOGRAPHIC HASH FUNCTIONS
These are more basic hash functions that are employed in hash tables, checksum creation, and data indexing. For the sake of simplicity or speed, they might give up some security features. MurmurHash, CityHash, and Jenkins Hash are a few examples.
- KEYED HASH FUNCTIONS
These hash functions, also known as HMAC (Hash-based Message Authentication Code), use a secret key alongside the input data. This offers integrity protection and authentication. HMAC-SHA256 and HMAC-MD5 are examples of keyed hash functions.
- CHECKSUMS
One kind of hash function used to confirm the integrity of data is the checksum. They are frequently employed as error detectors in data transfer protocols. Adler-32 and CRC32 (Cyclic Redundancy Check) are two examples.
- PASSWORD HASHING FUNCTIONS
Passwords can be safely stored with the help of these hash routines. To improve security, they frequently have features like stretching and salting. Bcrypt, Argon2, and PBKDF2 (Password-Based Key Derivation Function 2) are a few examples of it.
The most appropriate hashing algorithm to utilise will depend on the particular needs of the application, such as security, compatibility, and performance. Each type of hashing algorithm has advantages and disadvantages of its own.
HASHING USED FOR BLOCKCHAIN
Cryptographic hash functions are mostly employed in blockchain technology to secure transactions, maintain the immutability of the blockchain ledger, and guarantee data integrity.
Here are the main types of cryptographic hash functions commonly used in blockchain:
SHA-256 (Secure Hash Algorithm 256-bit)
Blockchain technology frequently uses SHA-256, particularly in digital currencies like Bitcoin. It is renowned for its robust cryptographic characteristics, such as collision resistance and pre-image resistance, and generates a fixed-size output of 256 bits.
SHA-3 (Secure Hash Algorithm 3)
NIST (National Institute of Standards and Technology) has standardised SHA-3 as the newest algorithm in the Secure Hash Algorithm family. It offers better security and efficiency than earlier SHA algorithms, that’s why blockchain applications are starting to use it more frequently.
MD5 (Message Digest Algorithm 5)
Message Digest Algorithm 5, or MD5, was in fact utilised in a few early blockchain applications. However, because of its vulnerabilities—especially with regard to collision attacks—its use in contemporary blockchain systems is incredibly uncommon. By using collision attacks, attackers can compromise the integrity and security of the system by identifying two distinct inputs that result in the same hash value.
RIPEMD-160 (RACE Integrity Primitives Evaluation Message Digest 160)
For the purpose of creating unique addresses from public keys, RIPEMD-160 is frequently used in conjunction with other cryptographic methods, especially in Bitcoin and other cryptocurrencies.
BLAKE2
A cryptographic hash function called Blake2 was created as a replacement for more older algorithms like SHA-256. It can be used in blockchain projects as a more effective hashing solution because of its great performance and security.
KECCAK
The fundamental hash algorithm used in SHA-3 is called Keccak. Although Keccak is defined by SHA-3 with a certain set of parameters, Keccak variants with other parameters can also be utilised in blockchain applications.
These cryptographic hash functions play a crucial role in distributed ledger systems’ security, decentralisation, and reliability as fundamental elements of blockchain technology. They are used in consensus processes, block validation, transaction verification, and the creation of cryptographic addresses, among other blockchain-related functions.
USE OF HASHING IN BLOCKCHAIN
In blockchain technology, hashing is essential because it performs a number of vital tasks that support the efficiency, security, and integrity of the network. Let’s Explore with me some of the major uses of hashing in blockchain applications:
DATA INTEGRITY
By creating unique fingerprints (hash values) for every block’s contents, hashing protects the integrity of data stored in blocks. Any change made to the data within a block would produce a completely unique hash value, which would alert everyone on the network to the change. This characteristic aids in preserving the blockchain ledger’s immutability.
BLOCK IDENTIFICATION
Every block on the blockchain is uniquely recognized by a hash value that is computed based on the contents of that block. This hash value is part of the block header and functions as a digital fingerprint for the block. It makes it simple for network users to recognize and refer to particular blockchain blocks.
CHAINING BLOCKS
Chaining blocks together in a sequential order is made easier via hashing. To create a linked list of blocks, each block has the hash of the previous block in its header. The chronological order of transactions is guaranteed by this chaining method, which also guards against tampering with previously validated transactions.
PROOF OF WORK (POW) MINING
Hashing is employed in the mining process of proof-of-work (PoW) blockchain networks, such as Bitcoin, in order to validate and append new blocks to the blockchain. By repeatedly hashing block headers with various nonce values until a hash value that satisfies specific requirements is found, miners compete to solve a cryptographic puzzle. This highly computational procedure makes sure the network is secure and decentralised.
ADDRESS GENERATION
Hashing techniques are frequently used in blockchain networks to generate cryptographic addresses, also known as public keys. For example, hashing algorithms such as SHA-256 and RIPEMD-160 are used to generate Bitcoin addresses from public keys. By doing this, it is ensured that every address is produced securely and uniquely from the associated public key.
CONCLUSION
The secret of the functioning of blockchain is hashing. Data integrity verification ensures that information is valid; block identification gives each block a unique ID; and secure block chaining securely connects the blocks. Even more, hashing facilitates consensus-building among computers on the network and generates the distinct addresses needed for sending and receiving cryptocurrency (address creation). All of this results in a decentralised, trustless, and unchangeable public record system that is impervious to tampering and doesn’t require a central authority.
If you want to learn about how blockchain works and how to use hash-functions algorithms, Please click on the link(www.drusmantahir.com)