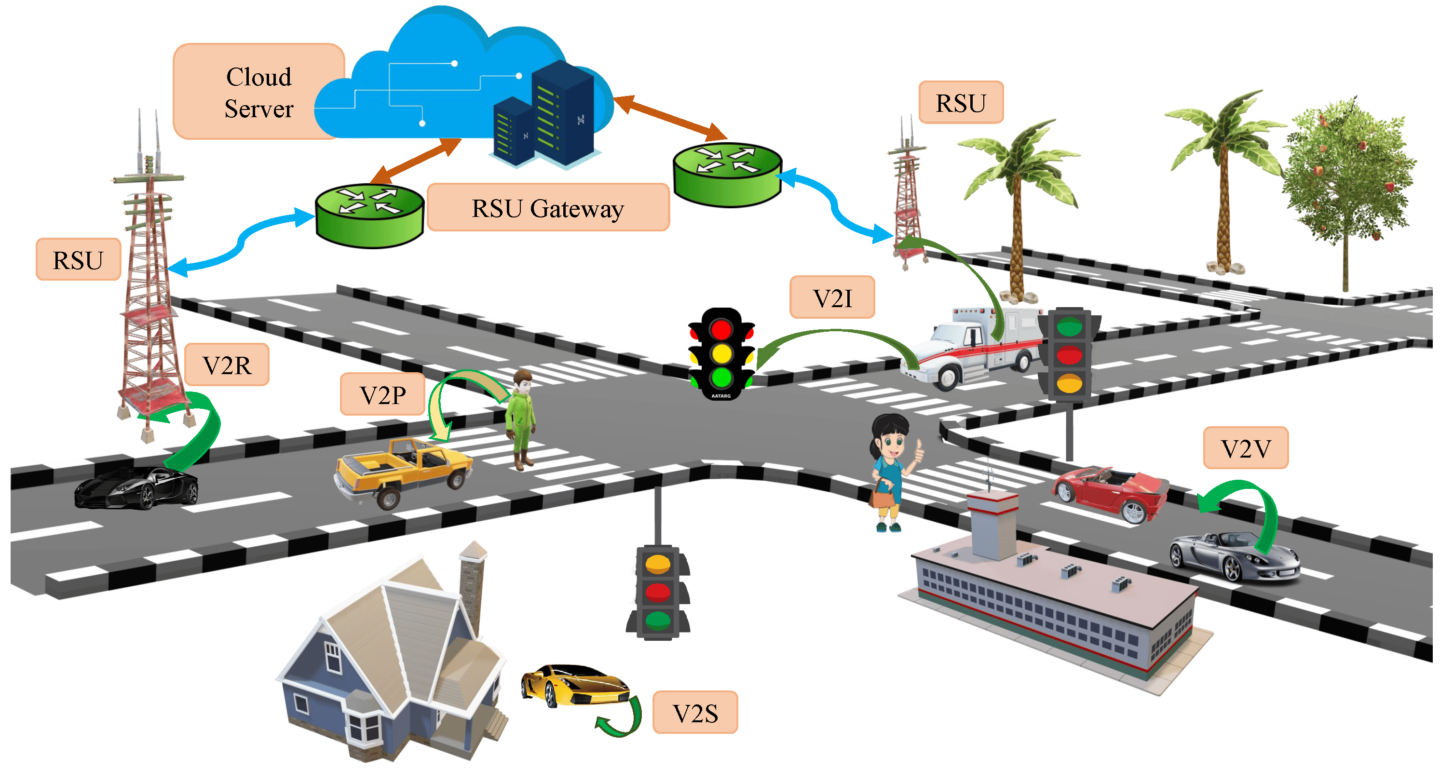
WHAT IS THE ROLE OF MACHINE LEARNING WITH THE INTERNET OF VEHICLES?
With the progression of technology and the increasing adoption of vehicles, the difficulties associated with transportation are getting increasingly complicated. The highways frequently experience congestion, accidents occur frequently, and the general traffic conditions are worsening. The changing urban mobility environment necessitates the development of creative solutions to improve the effectiveness and security of transport networks. To tackle these difficulties, a strategic method is needed that combines contemporary technology and sustainable methods to enhance the efficiency and satisfaction of those traversing the ever-changing urban transport system.
Intelligent transportation makes use of machine learning (ML) technology to enhance facilities, track vehicles, and prevent accidents. It reduces urban traffic jams by improving traffic network setup. Intelligent parking solutions for reservation services and car selection are also being investigated in smart cities. By investigating intricate relationships between highways, traffic, outside factors, and traffic crashes, machine learning approaches are altering smart transportation. To handle artery and signal disruption, a deep learning model with unsupervised feature learning and supervised fine-tuning modules is presented, while reinforcement training-based traffic signal management is employed.
Applications of machine learning in IOV
Intelligent IOV applications for traffic safety, harmful behaviors, and intelligent services are made possible by ML technologies in data mining, pattern recognition, and cognitive computing. It reduces consumption of energy while meeting traffic offloading limits, hence creating fresh prospects.
- Autonomous Smart Driving
Machine learning is critical in smart driving technologies because it allows cars to effectively observe and evaluate their environment. Integrating IoT with machine learning and smart computation can result in an intelligent driving system. ML algorithms accomplish tasks such as item recognition, identification, and vehicle location prediction. Making choices in self-driving cars necessitates the processing of input from several sources through the use of modular perception-planning-action or End2End learning.
- Deep Learning for Driver Support and Security
Deep learning predicts highway security indices by analyzing street technology, social behavior, and traffic patterns. Driver Assistance Systems (ADAS) use machine learning and embedded computers to recognize obstacles, map out routes, and enhance the precision of blind spot forecasts.
- Machine Learning in Smart Transportation
Intelligent transportation system (ITS) improves track, parking, and facilities by utilizing machine learning techniques. It makes use of IoT and machine learning to provide free parking, traffic monitoring, and performance tracking. Distributed systems deal with massive amounts of data while combining algorithm correctness and size.
Challenges
Vehicular systems, especially in the context of Intelligent Transportation Systems (ITS) and networked vehicles, face certain constraints that provide challenges to their efficient operation and adoption. Some of the limitations include:
- Vehicle Speed
Data interchange is additionally slowed by erratic speed of vehicles. Vehicle node mobility and network structure in vehicular networks make authentication and security problematic. Frequent modifications to network architecture disturb intrusion detection and security systems.
- Network Size
As the volume of internet data on the Vehicular network grows, so does processing and network protocol traffic, leading to higher safety protocol congestion, identification of errors, and network delay.
- Multicultural Framework
The V2V architecture, which consists of many nodes and dynamic networks, poses a substantial problem in comprehending the interrelated capabilities among vehicles for safe and authenticated applications.
- Confidential Responsibility
Authenticity and confidentiality of IoV nodes frequently serve as models using secure algorithms, however without data privacy assurance, security techniques frequently struggle to differentiate abnormalities and mistakes.
- Prerequisite for rapid reaction
For rapid modifications, the Internet of vehicular networks (IoV) requires immediate management. Although solutions like ECDSA and PKI protect anonymity, aggravating activities such as spoofing and wormhole attacks can be used. Authentication and detection are improved by machine learning approaches.
- IoV Verification Method
For Internet of Vehicles (IoV) networks, authentication techniques are critical for networking and communications safety. Computing identity and resource waste are two obstacles. By lowering expenses, AI methods can enhance anonymous verification. Although Certified Short Signature Models and Aggregated Privacy-Preserving Authentication decrease time delay, they demand a big amount of information. Artificial intelligence (AI) technologies such as Support Vector Machine and Pseudo-Random Binary Sequence improve IoV security by analyzing vital data and enabling self-adaptation for certification and permission. An SVM-based quant approach allows for a distinction of packed and sparse information.
- Fog-Based Identity Authentication
By facilitating connectivity between automobiles and clouds, fog computing in IoV applications lowers congestion. It improves security by utilizing deep learning for authentication of identities and machine learning for access control. AI and machine learning techniques provide a defense strategy.
Potential Solutions
The combination of machine learning with IoV offers increased efficiency, precision, and control over resources. ML collects large amounts of sensory input, improves decision-making, and supports the creation of 2D levels, forecasting, and cooperative mobility systems. AI technologies are being used in 5G and 6G networks for smart network management.
How ML developed a secure vehicular network for 6G technology?
The objective of the 6G vehicular network is to create a flexible and intelligent system capable of adjusting to different application demands and operation categories, including improved mobile broadband, highly dependable and low-latency interactions, and extensive machine-type communications. It distinguishes itself from traditional vehicular networks, which prioritize communications between V2V and V2I. The implementation of the 6G network has the potential to significantly enhance transportation, human contact, and human socialization.
Machine learning (ML) is an advanced Artificial Intelligence (AI) technique that improves several systems, such as pattern identification, natural language processing (NLP), autonomous driving, and gaming AI. Present machine learning methods prioritize data identification and swift correlation recovery, rendering them promising instruments for dynamic adaption, safe interaction, and prompt reaction in 6G intelligent vehicular networks. Applications encompass rapid channel equalization, adaptive distribution of resources, intelligent control of traffic, mobile computing, and detection of breaches in vehicle 6G networks.
In an ML-based assurance strategy, vehicular systems often require a large number of limitations.
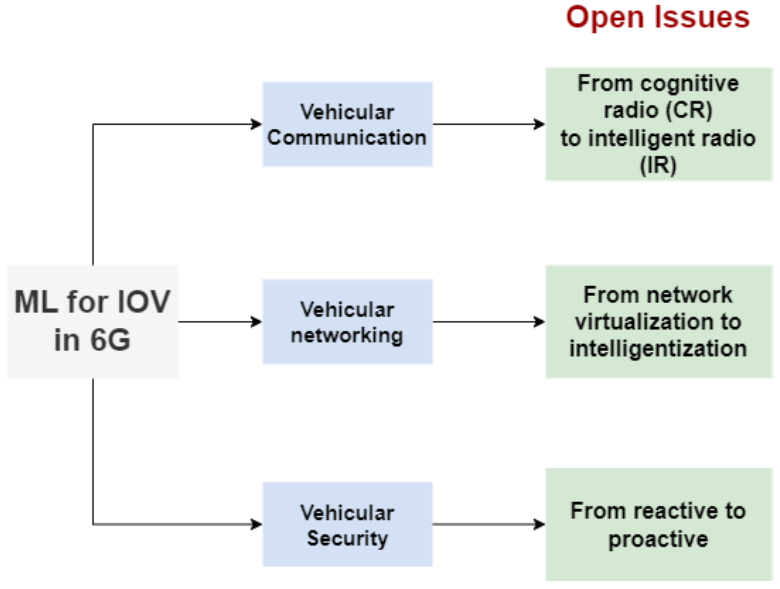
The adoption of 6G in vehicular networks is essential for addressing key challenges, including the advancement of Cognitive Radio (CR) to Intelligent Radio (IR) in communication, the shift from virtualization to intelligentization in networking, and the transition from a reactive to a proactive security paradigm in vehicles. It is crucial to tackle these modifications in order to establish a safe, intelligent, and high-performing environment. The future of vehicle communication will be shaped by creative approaches, namely those that utilize powerful machine learning technology and intelligent network architecture. The success of 6G networks will be determined by effectively incorporating intelligent solutions to address difficulties in CR, IR, virtualization, and proactive strategies.